
Frequently Asked Questions About Digital Risk Protection (DRP)
This page has been peer-reviewed, fact-checked, and edited by qualified attorneys to ensure substantive accuracy and coverage.
If you are like most of the world, 2020 likely had a life-changing impact on the way you interact with others, conduct business, and consume content. Unfortunately, these changes have also led to an increase in cybercrime, hacking, sextortion, online extortion, and internet blackmail.
In this article, we address the most common questions about digital risk protection (DRP), including:
- How to determine if you need digital risk protection;
- How effective DRP strategies are against data privacy breaches;
- How to get started with digital risk protection and find the DRP service that is right for you.
As internet attorneys, we at Minc Law have seen digital risk protection become a common topic of interest for our clients. It has become a top priority to give our clients peace of mind knowing their online reputations are being protected. That is why we developed a robust digital risk protection service to monitor and eliminate online threats.
Below, we begin with a discussion of what digital risk protection is, how to know if you need DRP, and how to assess your own cyber risk levels.
Let us help. Contact us for a free consultation with an intake specialist to help you explore your removal options and craft an effective strategy.Are you the target of defamation?
Why Do I Need Digital Risk Protection?
As internet attorneys, our client conversations often turn to the subject of digital risk protection (DRP). For instance, many clients ask:
- “What is digital risk protection, and why do I need it?”
- “How do I assess my cybersecurity risk and perform a security assessment?”
- “How effective are digital risk protection strategies against data privacy breaches?”
We address all three questions below.
Sometimes, our clients are proactive in searching out DRP. These clients know that their brand is being discussed and engaged with online. Others are more reactive, contacting us after experiencing a cyberattack or threat to their brand or personal reputation. These clients might remain unsure if the perpetrator is still attacking them or if someone else is defaming them online.
Regardless of how you began searching it out, you need DRP if it is your goal to monitor and identify specific threats and digital risks as soon as they happen.
What is Digital Risk Protection?
Digital risk protection (DRP) is a holistic approach to monitoring and identifying threats against your digital assets. It is the act of using technology, tools, and expertise to monitor data sources for threats to your or your organization’s digital footprint.
The internet is a vast frontier that humans are still learning to explore—similar to outer space. And how DRP experts go about protecting your most important assets is no different than the way NASA plots a precise course for its astronauts.
Because not every situation is one that can be protected or monitored against, DRP comprises multiple strategies and tools. Digital risk protection experts first need to understand:
- Your unique situation,
- The digital assets that are most important to you, and
- If any existing or known risk is impacting your brand or reputation online.
Digital risk protection is about developing a strategy to protect what is most important to you. It is also about how that threat is handled in the event that it requires remediation or litigation.
Video: What is Digital Risk Protection? Minc Law’s DRP Service Explained

Why Should You Use Digital Risk Protection?
Increased interconnection comes with countless benefits. It also comes with an increased risk of your online presence being used against you. According to non-partisan think tank Pew Research Center, 41% of American adults have experienced online harassment. Also, roughly six in ten Americans believe it is impossible to go through their daily lives without their online data being collected.
As our lives become digitized, more professionals recognize the risks caused by online threats. According to a 2019 study by RSA Security, 26% of respondents felt that digital risks were expanding at a faster rate than they could fight them.
Digital risk protection is one of the fastest-growing trends relating to cybersecurity. It will become more pervasive as more of our activities are tied to the internet. Such digitization of our lives opens new doors for threats, attacks, and risk.
In many ways, DRP is no different than a car alarm, home security system, or identify theft technology. It protects what is most important to you.
When Should You Start Securing Your Digital Transformation Initiatives?
The best time to start securing your digital presence is right now. Cybersecurity and threat intelligence are rising trends. Many organizations are evaluating their digital and information security due to the effects the pandemic had on their brand.
They understand the threat to their digital security, and they are concerned. But this concern does not mean that they always know when they are at the most risk—or what they can do to protect themselves.
Act as soon as possible to shore up your defenses by following the tips described below in this article. Then, make it a habit to audit your digital presence at least once every quarter by:
- Updating passwords,
- Deleting old accounts,
- Removing yourself from directory sites, and
- Monitoring anything involving your identity or brand that is being discussed online.
How Do I Know If I Am Ready For Digital Risk Protection?
Our clients have a tendency to buy DRP services at different stages of the risk experience. These clients generally fall into three groups:
- Those who are proactive. These individuals and businesses may not have experienced a cyber attack or threat to their digital presence. Yet, they are aware of the risks and want to be prepared (or better yet, prevent cyber threats altogether).
- Those who are reactive. Some organizations or individuals look into DRP services after becoming victims of a cyberattack. This threat may be identity theft, sensitive information leaks, or cybersquatting.
- Part of a larger strategy. These entities are developing a strategy for their digital presence, reputation, and cybersecurity. They are aware of the constantly-evolving state of technology in the digital age. They want to be as prepared as possible to meet the future head-on while protecting their most valuable digital assets.
There are many scenarios that could prompt one to embrace DRP, but that does not mean it is right for everyone. For instance, those who do not have a web presence or who are not worried about their digital risk may not need DRP. Some individuals simply do not have the extra money to spend on this service.
For everyone else, you will generally know you are ready to consider DRP if you have a high amount of cybersecurity or digital risk. You may have been hit with a digital attack recently or in the past. Or, you may want to be proactive and find reasonable ways to protect yourself against this growing threat.
How Do You Assess Cybersecurity Risk?
In its simplest explanation, cybersecurity risk assessment means understanding the assets you own in a virtual world that could be attacked by an entity looking to do harm to you or your brand.
An assessment of your cybersecurity entails mapping out, managing, identifying, and controlling your mitigation efforts. This process will also help you or your organization create safeguards for your data and identify areas that are open to threats.
Individuals and businesses assess their cybersecurity risk based on:
- Their industry,
- The size of their organization,
- Whether or not they have been a victim of attacks before,
- Whether they have a high profile online.
Conduct an assessment of your various cyber risks and identify whether you comply with best practices and standards. This assessment can be done internally, or you can hire external security risk assessors to do it for you.
How Do You Perform a Security Assessment?
Generally, security assessments and audits are tailored to businesses and brands. However, the reality is that they are equally applicable to individuals, even if not to the same degree.
To assess your security status and susceptibility to threats:
1. Review Existing Security Policies
If you are a company or brand, that is an internal document or policy typically.
As an individual, this will be more about listing all out all your software platforms and security tools you are currently utilizing for any protection and what current security settings are currently activated.
2. Take Inventory of Your Online Presence
Take an inventory of your tools, software, technology, and the online accounts that impact you or your business or present vulnerability.
3. Create a Diagram of Your Digital Assets
Create a diagram of your network and digital assets so that it is easier to understand their interconnectivity and potential vulnerability points.
4. Assess the Complete Scope of Your Network & Assets
Ask yourself the following questions to ensure you are seeing the fullest picture possible:
- Do you currently have a way to deal with your (or your customers’) sensitive data?
- What information can the public, your employees, or other people access?
- What are your remote work policies for accessing network information?
- Do you currently have a procedure for responding to cyberattacks or a breach in security?
5. Consolidate Your Security Policies
Compile your cybersecurity policies into one centralized location, document, or handbook. That way, everyone in your organization can be on the same page.
6. Assess Past & Present Threats
Take into account the threats that exist today or that have existed in the past. Are there areas of primary concern that you should keep in mind?
7. Prepare For a Worst Case Scenario
Determine the potential impact on yourself or your business if something does go wrong. These incidents could take the form of defamation, impersonation, extortion, or a ransomware attack.
8. Prioritize Your Digital Assets
Prioritize which digital assets to secure and protect first. What options exist to do so, and how do you remediate in the event that a worst-case scenario does happen?
9. Develop & Implement a Cybersecurity Protocol
Develop a cybersecurity protocol supported with tools such as digital risk protection. Implement a plan for regular security audits, including monitoring your cybersecurity controls.
10. Optimize & Remediate Security Practices & Problems
Make sure to regularly optimize your security practices and remediate any problems that arise.
Minc Law Cybersecurity Fact: While the terms “cybersecurity assessment” and “cybersecurity audit” are often used interchangeably, they are technically different. An assessment is a high-level evaluation of your cyberhealth and how vulnerable you are to risk, including determining the effectiveness of any security measures currently being used. An audit, on the other hand, is a point-in-time check to determine whether you have certain safeguards in place and how well they are functioning.
When Should You Start Increasing Your Digital Risk Protection?
Knowing when to take precautions is important as you embrace DRP to safeguard your most important online assets.
It is easy to feel a stronger sense of urgency when you discover a vulnerability or fall prey to attack. However, many individuals or businesses need to increase their DRP proactively before being hit by these threats or vulnerabilities in the first place.
If you are unfamiliar with DRP and don’t know where to start, it’s important to rely on digital risk protection experts to guide you through what’s important. When engaging with a DRP service like Minc Law, our experts will help guide your protection strategy and advise you what resources should be utilized to increase your protection when it’s needed.
At Minc Law, our experienced internet attorneys and search analysts can help determine the technology that is needed to mitigate risk and identify threats. They will also watch for an uptick in threats and determine whether there is a need for a responding increase in protection efforts.
How Effective Are Digital Risk Protection Strategies Against Data Privacy Breaches?
As digital risk protection strategies improve, so do the tactics used by hackers and online scammers. There will never be a strategy that provides complete, 100% protection against risk.
There are, however, several key technologies and strategies that can help you lower your risks and vulnerabilities.
Which Data Security Technologies Can Help Mitigate Risk?
When it comes to protecting your digital assets from attack, there are numerous tools from which to choose. While hiring a DRP service is a more holistic approach, you can always employ one (or several) of these tools to mitigate your risk in the meantime.
Antivirus Software
One of the simplest ways to begin protecting against external threats is to use a top-rated antivirus software. Most antivirus protection tools come with regular updates that address the latest known cyber threats.
Antivirus software protection tools monitor your devices for recognized virus signatures. They then block and prevent many viruses from spreading throughout your network.
Local & Cloud-Based Technology Backup Services
Guarding against viruses is not always enough for some individuals with a substantial digital presence. A backup strategy, whether it be in the cloud or on a physical server, helps you create backup copies of your valuable assets in case of loss or compromise.
A few backup options for businesses and individuals include:
- USB drives;
- An external hard drive;
- Local Area Network (LAN) or Network Attached Storage (NAS);
- Online backup tools such as iDrive, SOS Online Backup, or Acronis True Image.
Virtual Private Network (VPN)
A virtual private network (VPN) obscures your location and encrypts your internet activity data. This tool helps protect you from malicious individuals who might snoop on your internet activity. VPNs also protect you from your internet service provider (ISP), which may be selling your browsing data.
Some of the most popular VPN services include ExpressVPN, Norton Secure VPN, and Surfshark.
Encrypted Managed Password Storage Banks
One simple way to safeguard your online assets is to protect your passwords. A quality password manager such as LastPass, Dashlane, or TrueKey will generate strong passwords for you. These tools also store those passwords in a secure, encrypted vault.
DDoS Protection
A distributed denial-of-service (DDoS) attack is a hostile disruption of a server or network by flooding it with traffic. This act of overwhelming the target server or network leaves it more vulnerable to infiltration.
To protect your assets from DDoS onslaughts, it is wise to use tools such as Cloudflare to absorb network overload. For example, Cloudflare is a content delivery network that spreads out the distribution of your content globally, caching it (content) on servers around the world to speed up website times and prevent network overload.
Surface & Dark Web Monitoring Alert Systems
Those who worry about exposure and attack on the dark web invest in dark web monitoring alert systems such as LastPass, Webhose.io, and ID Agent.
These tools watch for leaked business information or sensitive data. They can help reduce business risk and reputation damage from this leaked data on the deep or dark web.
Multi-Factor & Two-Factor Authentication
Multi-factor authentication (MFA) and two-factor authentication (2FA) tools help secure your digital assets. They require layers of confirmation before accessing them. For instance, a user may enter the password, then enter a code that was sent to a 3rd party in real-time, such as a mobile phone.
Some of the most popular MFA and 2FA tools include Duo Security, Google Authenticator, and Authy. As SIM swapping attacks have become more prominent over the years, avoid using SMS 2FA to secure your digital assets.
Digital Risk Monitoring Tip: Sometimes, the best first step is the simplest. Be prepared for a security breach by consistently monitoring your profile with paid software or through Google Alerts. This preliminary observation will give you important information about your digital risk.
What Are the Different Digital Risk Protection Strategies?
The strategy you employ to protect your digital assets depends on the threats that are your greatest concern or what your biggest assets are and their location and environment. In general, the common digital risk protection approaches fall into one of three categories:
- External threat mitigation. Your strategy may focus on outward threats, such as threats on social media, attacks from the dark web, phishing attempts, executive impersonations, trademark infringement, counterfeits, and ransomware.
- Internal threat mitigation. This strategy focuses on keeping internal vigilance against allowing viruses and malware past your defenses. Internal threat mitigation involves avoiding weak security protocols, watching for bad actor employees compromising your internal safety, and training employees not to fall for phishing emails or use weak passwords.
- Compliance-based threat mitigation. In some industries, you must follow standard regulations (e.g., HIPPA for a health organization or FINRA for a financial company) to avoid fines.
Which Digital Risk Protection Strategies Are the Most Effective?
When attempting to protect your digital assets or online reputation, it is generally advisable to use a balanced approach. Address external threats, internal weaknesses, and compliance-based requirements as needed.
Regardless of your individual focus and priorities, the best strategy is to proactively monitor for threats. Then, conduct quarterly audits to understand where your weaknesses are and what you can do to mitigate and guard against them.

Getting Started With Digital Risk Protection & Finding a DRP Service That is Right For You
Starting out with a DRP service can be very straightforward, depending on your situation and immediate (and long-term) goals. Involving DRP experts maximizes both the efficiency of the process and the potential for protection.
How Do You Know Whether or Not You Need Digital Risk Protection?
Digital risk protection services can solve one of your biggest causes for concern. You may be losing sleep at night from being worried about your brand being under attack online—and you may feel helpless about how to control it.
The internet is a large place, and digital risk protection services vary widely. When choosing the right DRP solution for you, your first priority should be ensuring that it will protect what you are trying to protect. Next, focus on learning what happens after a threat is identified.
Digital risk protection is about more than having world-class technology with which to monitor threats. It requires a sound strategy that focuses on key data sources that can be filtered and scanned. Ultimately, the best way to find out whether DRP is right for you is to schedule a demonstration and to speak with your DRP specialist.
How Do You Get Started With Digital Risk Protection at Minc Law?
Minc Law’s Digital Risk Protection service is a turn-key solution for individuals and businesses alike where your account manager does most of the heavy lifting for you.
After your purchase, an email from our principal attorney, Aaron Minc, will walk you through the onboarding process. You will also receive as part of that email a link to an onboarding questionnaire. This questionnaire outlines and assesses the foundation of your digital profile and takes 15–20 minutes to complete.
Once the questionnaire is submitted, it will take 3–5 business days for your profile to be created. One of our search analysts and paralegals will be in contact to answer any questions and schedule our first onboarding call.
We will then confirm that we have all your personal information, social media accounts, and images. This confirmation helps ensure a properly authenticated account.
Approximately 7–10 days after your first call, your account representatives, who will be an assigned Minc Law paralegal, attorney, and/or ZeroFox OnWatch™ specialist, will send you a customized report. During your second onboarding call, we will review and discuss this report. At this point, we work to ensure an optimal profile, workflow, and strategy. Our search analyst team will be in touch with you constantly to ensure that we are focused on protecting what matters most to you.
How Do You Know if Your Digital Risk Protection is Working?
We cannot speak to other digital risk protection services. However, as a subscriber to Minc law’s Digital Risk Protection (DRP) service, you will receive two monthly reports:
The first is your Protected Executive Report, which is a snapshot of your digital profile and assets being monitored within Zerofox and other platforms.
The second is an Alert Detail Report showing activity located regarding your account in the last 30 days. These alerts are not usually actionable threats, but provide visibility into the activity we are monitoring and work being conducted.
An example of a ‘Name and Image’ alert detected by our digital risk protection service highlighting the content ‘type’ and URL, ‘risk rating’, and status of threat remediation.
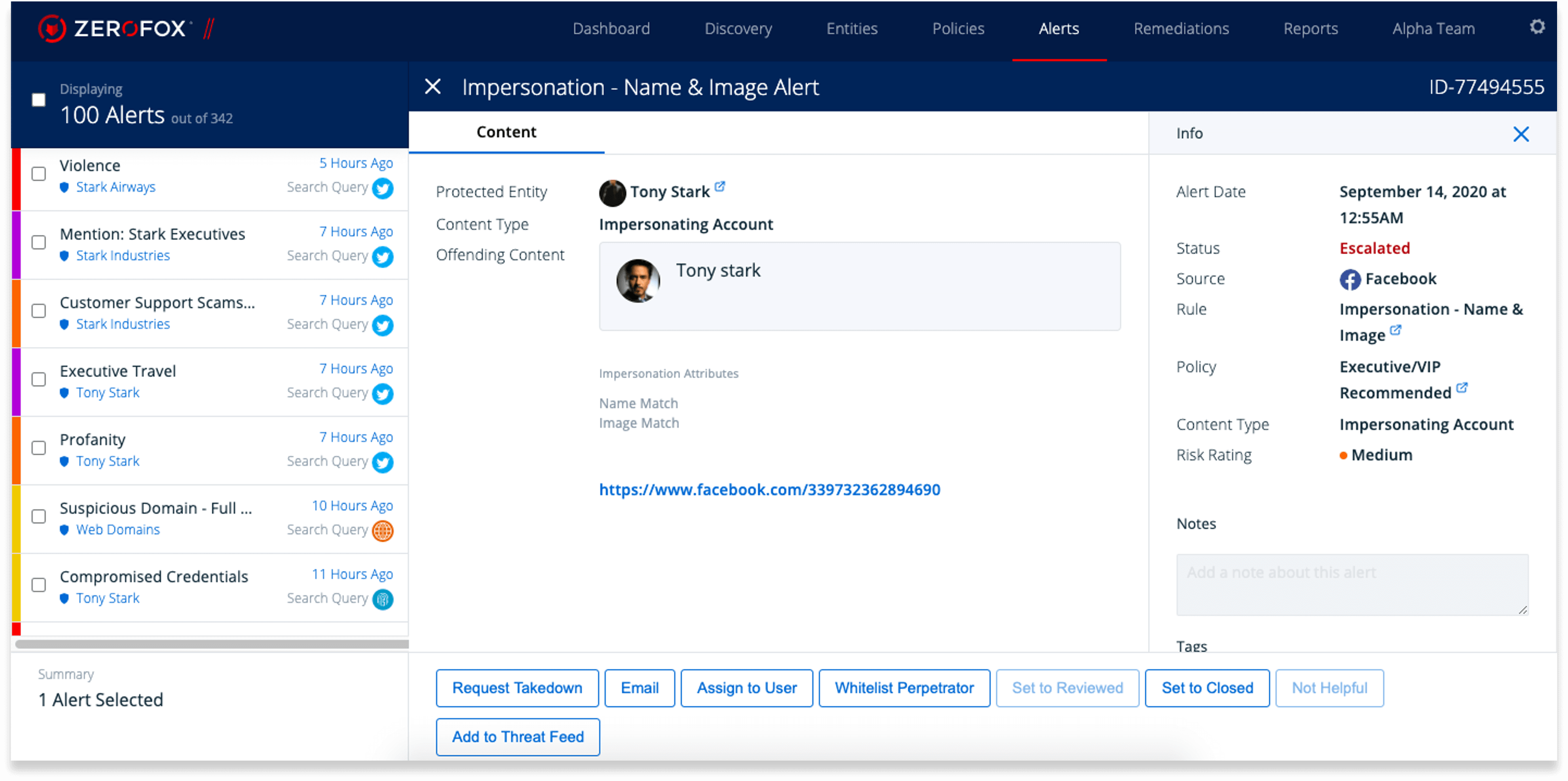
Reviewing these reports should give you an idea of how well your digital profile is being monitored and protected.
Our detection system uses a two-tiered system of alerts. The first line of defense is an artificial intelligence threat platform. This AI grows smarter as it becomes acquainted with your digital profile and associated risks.
Video: Understanding Your Digital Risk Protection Alerts

The second tier is a search analyst from the ZeroFOX OnWatch team. These individuals are experts at uncovering potential threats and concerning online activity. In those cases, a real-time email alert will be generated similar to the example below. Again, these results do not necessarily require immediate action, rather important for you to k.
Finally, the last way to know if DRP is not working for you is if you are still questioning your digital footprint and losing sleep in relation to that. If you have not gained some semblance of peace of mind, perhaps DRP was not the solution you needed.
Digital Risk Protection: Safeguard Your Digital Presence With Minc Law
It is becoming ever more necessary in today’s increasingly online world to protect your digital footprint. At Minc Law, we believe in helping our clients safeguard their digital assets with robust monitoring services and tools.
★★★★★
“The DRP takedown through ZeroFox did for $500 what I paid my previous representation over $2,000 for. The previous representation did not succeed, but ZeroFox did.”
K, March 15, 2021

If you are ready to take the next step to protect your digital assets, you can schedule a demo here. You can also sign up for a 45-day, money-back-guaranteed trial or schedule a consultation with one of our intake specialists.





